A strong SOC analyst resume is your first step toward securing a role as a security operations center specialist.
In this competitive field, your professional resume needs to not only highlight your technical skills but also demonstrate your ability to handle real-time cybersecurity threats.
In this article, we’ll explore the essential resume sections of a great document, offering expert tips to help you stand out to hiring managers.
SOC analyst resume examples
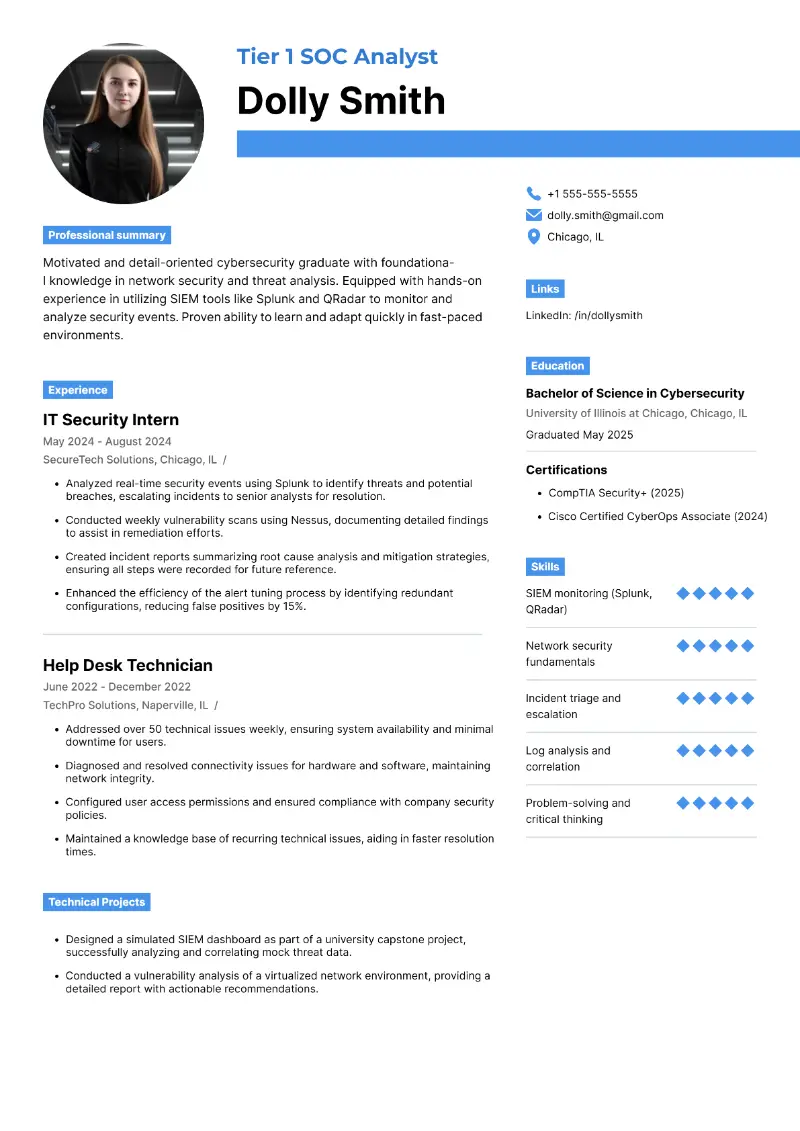
Tier 1 SOC analyst resume sample
Entry-level SOC analyst resume template
Resume for SOC analyst | Plain text
Dolly Smith
Email: dolly.smith@gmail.com | Phone: +1 555-555-5555 | LinkedIn: /in/dollysmith | Location: Chicago, IL
Resume Summary
Motivated and detail-oriented cybersecurity graduate with foundational knowledge in network security and threat analysis. Equipped with hands-on experience in utilizing SIEM tools like Splunk and QRadar to monitor and analyze security events. Proven ability to learn and adapt quickly in fast-paced environments.
Skills
- SIEM monitoring (Splunk, QRadar)
- Network security fundamentals
- Incident triage and escalation
- Log analysis and correlation
- Problem-solving and critical thinking
- Endpoint protection strategies
- Firewall configuration basics
- Risk assessment support
Experience
IT Security Intern
SecureTech Solutions, Chicago, IL (May – August 2025)
- Analyzed real-time security events using Splunk to identify threats and potential breaches, escalating incidents to senior analysts for resolution.
- Conducted weekly vulnerability scans using Nessus, documenting detailed findings to assist in remediation efforts.
- Created incident reports summarizing root cause analysis and mitigation strategies, ensuring all steps were recorded for future reference.
- Enhanced the efficiency of the alert tuning process by identifying redundant configurations, reducing false positives by 15%.
- Collaborated with the SOC team to simulate phishing attacks, raising awareness and improving user response protocols.
Help Desk Technician
TechPro Solutions, Naperville, IL (June – December 2023)
- Addressed over 50 technical issues weekly, ensuring system availability and minimal downtime for users.
- Diagnosed and resolved connectivity issues for hardware and software, maintaining network integrity.
- Configured user access permissions and ensured compliance with company security policies.
- Maintained a knowledge base of recurring technical issues, aiding in faster resolution times.
- Assisted in deploying antivirus and endpoint security tools across user systems.
Education
Bachelor of Science in Cybersecurity
University of Illinois at Chicago, Chicago, IL (Graduated May 2025)
Certifications
- CompTIA Security+ (2025)
- Cisco Certified CyberOps Associate (2024)
Technical Projects
- Designed a simulated SIEM dashboard as part of a university capstone project, successfully analyzing and correlating mock threat data.
- Conducted a vulnerability analysis of a virtualized network environment, providing a detailed report with actionable recommendations.
Strong sides of this IT security analyst resume example:
- Highlights practical experience with SIEM tools and vulnerability scanning, showcasing a solid foundation for entry-level roles.
- Demonstrates relevant internships that bridge academic knowledge and real-world application.
- Includes technical projects that emphasize hands-on problem-solving and industry-relevant skills.
How to properly format a resume
A professional design ensures your qualifications are easy to read and quickly understood by hiring managers.
- Use clean fonts like Arial, Calibri, or Times New Roman in 10–12 point size.
- Stick to one page resume unless you have extensive experience (10+ years), in which case two pages are acceptable.
- Add standard 1-inch margins for a balanced appearance.
- Divide your document into clear sections with bold headings (e.g., Summary, Skills, Experience, Education).
To avoid formatting issues, use an online resume helper.
Resume Trick simplifies the writing process, offering free modern resume templates tailored to different roles.
Create your professional Resume in 10 minutes for FREE
Build My Resume
Tier 2 SOC analyst resume example
Sample experienced SOC analyst resume
Sophia Carter
Email: sophia.carter@gmail.com | Phone: +1 404-555-9876 | LinkedIn: /in/sophiacarter | Location: Atlanta, GA
Resume Summary
Proactive and experienced SOC Analyst with over 9 years of expertise in investigating complex security incidents and performing forensic analysis. Adept at using advanced tools and methodologies for threat detection, response, and mitigation. Proven ability to improve team workflows, mentor junior analysts, and leverage threat intelligence to bolster organizational security.
Skills
- Threat intelligence analysis
- Advanced incident response
- Forensic investigations
- Vulnerability assessment tools (Nessus, Qualys)
- Scripting (Python, PowerShell)
- Malware reverse engineering basics
- Network traffic analysis (Wireshark, TCPdump)
- Security Information and Event Management (SIEM) tuning
Experience
SOC Analyst (Tier 2)
CyberShield Technologies, Atlanta, GA (July 2020 – Present)
- Conduct deep-dive investigations into escalated incidents, resolving 95% of threats within SLA timeframes.
- Automate repetitive log analysis tasks with Python scripts, improving analysis speed by 30%.
- Develop training materials and lead weekly sessions to upskill Tier 1 analysts in incident escalation protocols.
- Monitor threat intelligence platforms to preemptively address risks, preventing at least 10 potential breaches annually.
- Collaborate with threat hunting teams to identify and contain advanced persistent threats (APTs).
Information Security Analyst
SouthernTech Inc., Savannah, GA (March 2018 – June 2020)
- Performed regular vulnerability scans and collaborated with IT teams to remediate identified risks, reducing exposure by 25%.
- Managed and analyzed firewall logs, identifying unusual patterns that indicated unauthorized access attempts.
- Investigated phishing campaigns, identifying compromised credentials and mitigating potential data leaks.
- Implemented endpoint protection tools across the organization, decreasing malware incidents by 30%.
- Assisted in designing network segmentation strategies to limit lateral movement of threats.
IT Support Specialist
TechSecure Systems, Atlanta, GA (August 2016 – February 2018)
- Provided Level 2 support for technical issues, resolving complex problems and reducing escalation rates by 20%.
- Configured access control systems for 200+ users, ensuring adherence to security policies.
- Supported the deployment of IDS/IPS tools and provided feedback on their configuration.
- Maintained a detailed incident log that improved the efficiency of future troubleshooting efforts.
- Facilitated user training sessions on security awareness and best practices.
Education
Bachelor of Science in Computer Science
Georgia Institute of Technology, Atlanta, GA (Graduated May 2020)
Certifications
- Certified Ethical Hacker (CEH) (2023)
- Splunk Core Certified Power User (2020)
Community Involvement
- Volunteered as a cybersecurity mentor for Atlanta Cyber Youth Initiative, guiding high school students through basic cybersecurity concepts and challenges.
This example of a SOC analyst resume will impress recruiters:
- Showcases advanced technical skills like scripting and forensic analysis, appealing to mid-level SOC roles.
- Includes leadership activities, such as mentoring junior analysts and leading training sessions, demonstrating professional growth.
- Balances expertise with certifications and community involvement, reinforcing dedication to the field.
Should I choose a SOC analyst resume objective or summary
- Ideal for seasoned SOC analysts.
- Provides a concise overview of your skills, achievements, and experience.
SOC analyst resume summary sample:
Certified SOC Analyst with 5+ years of experience in threat detection and incident response. Proficient in SIEM tools and network security. Successfully mitigated 30+ cyber threats in the past year.
- Best for entry-level candidates or career changers.
- Highlights your goals and what you bring to the role.
SOC analyst resume objective example:
Dedicated cybersecurity graduate seeking a SOC Analyst role to leverage skills in threat monitoring, vulnerability assessment, and incident response to protect organizational assets.
How to organize your SOC analyst resume skills
The skills resume section highlights your expertise and interpersonal abilities, making it crucial for any application. Employers need to see at a glance that you have the qualities to excel in the role.
- Hard skills for resume are technical capabilities directly relevant to the job.
- Soft skills for resume are personal attributes that enhance your effectiveness.
SOC analyst hard skills:
- SIEM tools (Splunk, QRadar)
- Threat detection and response
- Malware analysis
- Network security monitoring
- Incident management
- Penetration testing
- Vulnerability assessment
- Forensic analysis
- Scripting languages (Python, Bash)
- Firewalls and IDS/IPS
Soft skills for SOC analyst:
- Critical thinking
- Problem-solving
- Communication
- Team collaboration
- Adaptability
- Attention to detail
- Time management
- Decision-making
- Stress management
- Continuous learning
Tier 3 SOC analyst resume template
Tier 3 SOC analyst resume sample
Resume for Tier 3 SOC analyst | Text version
Michael Harris
Email: michael.harris@gmail.com | Phone: +1 212-555-7890 | LinkedIn: /in/michaelharris | Location: New York, NY
Resume Summary
Senior SOC Analyst with over 12 years of experience in advanced threat detection, incident response, and cybersecurity strategy development. Skilled in managing high-severity incidents, leading cross-functional response teams, and implementing enterprise-wide security solutions. Proficient in cloud security, malware reverse engineering, and developing threat-hunting strategies.
Skills
- Advanced threat hunting
- Malware reverse engineering
- Security architecture and design
- Incident response leadership
- Cloud security (AWS, Azure)
- Endpoint Detection and Response (EDR) technologies
- Digital forensics and evidence preservation
Experience
Senior SOC Analyst (Tier 3)
Fortify Networks, New York, NY (March 2018 – Present)
- Lead a team of six analysts in identifying and mitigating advanced persistent threats, successfully neutralizing 15+ critical incidents annually.
- Design a next-generation SIEM implementation strategy, increasing detection accuracy by 40%.
- Collaborate with executive leadership to develop cybersecurity policies and response playbooks.
- Present forensic analysis findings to clients, assisting in legal proceedings and compliance audits.
- Spearheaded the deployment of cloud-native security monitoring tools, reducing alert noise by 25%.
SOC Analyst (Tier 2)
ShieldSec Corp., Newark, NJ (June 2015 – February 2018)
- Managed escalated incidents involving ransomware, reducing downtime by 50% during recovery.
- Performed in-depth forensic analysis of compromised systems, enabling root cause identification.
- Improved vulnerability management practices, achieving a 30% reduction in unpatched systems.
- Trained junior analysts on the use of advanced forensic tools and malware analysis techniques.
- Integrated threat intelligence feeds into SIEM platforms to enhance proactive detection capabilities.
IT Security Specialist
DataSecure Systems, Jersey City, NJ (January 2013 – May 2015)
- Built and maintained network security infrastructure for multiple clients, enhancing overall resilience.
- Conducted penetration tests and delivered actionable reports, reducing vulnerabilities by 35%.
- Investigated security breaches, ensuring affected systems were remediated promptly.
- Developed tailored security solutions for small and medium-sized enterprises, improving client satisfaction.
Education
Master of Science in Cybersecurity
New York University, New York, NY (Graduated May 2015)
Bachelor of Science in Computer Science
Rutgers University, Newark, NJ (Graduated May 2013)
Certifications
- Certified Information Systems Security Professional (CISSP) (2024)
- GIAC Certified Incident Handler (GCIH) (2023)
- Offensive Security Certified Professional (OSCP) (2021)
Publications
- “Advanced Threat Hunting: Techniques and Tools for Modern SOC Teams” published in CyberDefense Journal (2025).
- Co-authored a whitepaper on Cloud Security Best Practices, presented at the RSA Conference (2021).
This sample security analyst resume is effective for several reasons:
- Features extensive experience managing teams and responding to high-severity incidents.
- Demonstrates expertise in advanced threat hunting and security architecture, appealing to senior-level positions.
- Incorporates thought leadership through publications and conference presentations, highlighting industry recognition.
What academic credentials should I add to my resume
The education resume section demonstrates your foundational knowledge in cybersecurity and related fields. Employers want to know you possess the background to handle the technical demands of the job.
- List your degree(s) in cybersecurity, computer science, or related fields. Add the institution name, location, and graduation date.
- Showcase industry-recognized certifications on resume (e.g., CompTIA Security+, CEH, CISSP).
- Mention key courses on resume such as Cybersecurity Fundamentals, Network Security, or Incident Response if you’re an entry-level candidate.
Experience in an information security analyst resume
- State your most recent experience first.
- Include your role title, the company name, and the dates of employment.
- Highlight measurable accomplishments to demonstrate your impact.
- Adjust your experience to align with the job posting. Use relevant keywords to pass ATS screenings.
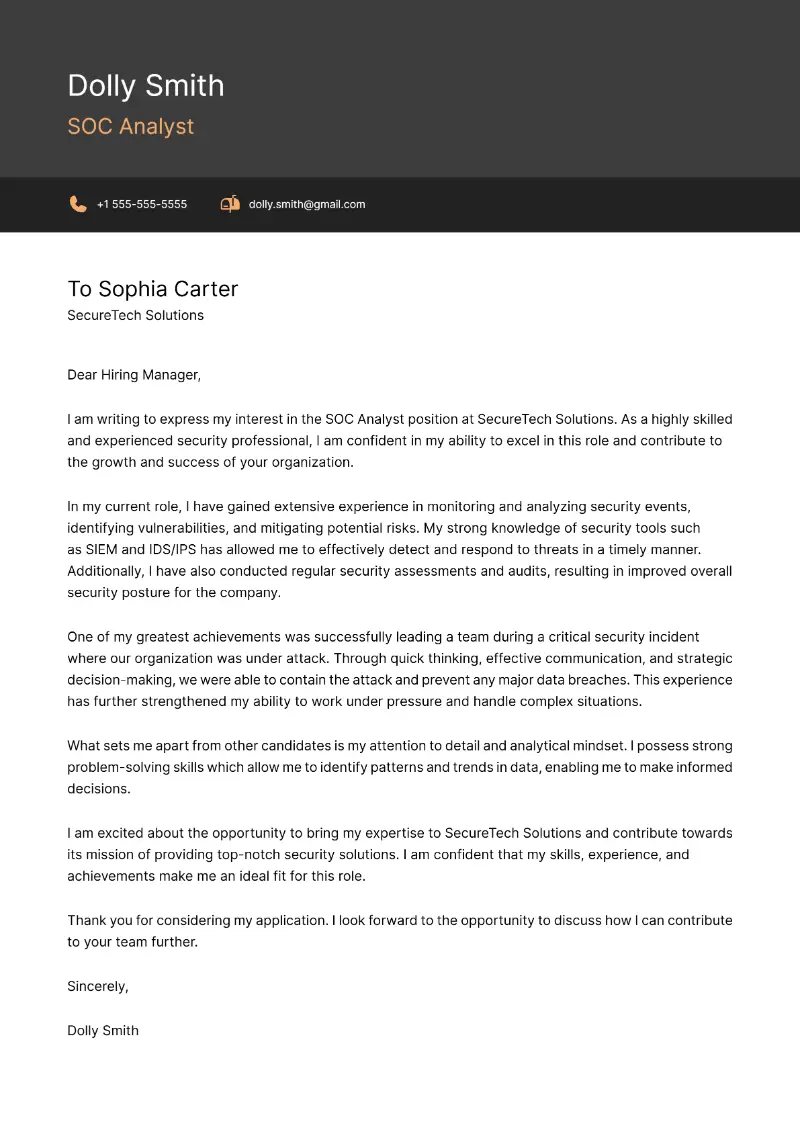
Cover letter for SOC analyst
A cover letter is a formal document that accompanies your resume when applying for a job.
Create your professional Cover letter in 10 minutes for FREE
Build My Cover Letter
How to write a SOC analyst cover letter:
- Customize it to the specific role, emphasizing relevant expertise in monitoring, analysis, and security.
- Begin with a compelling introduction, stating your interest in the position and company.
- Highlight your experience with threat detection, incident analysis, and utilizing security tools.
- Emphasize your critical thinking and ability to manage high-pressure situations effectively.
- Conclude by expressing enthusiasm for the opportunity and inviting a chance for further discussion.
SOC analyst cover letter example:
Conclusion
Creating a well-rounded resume requires more than just listing your technical skills.
By showcasing your certifications, experience in threat monitoring, and problem-solving abilities, you can create a document that makes a lasting impression.
Follow the guidelines in this article, and you’ll be well on your way to landing your next cybersecurity role.
Create your professional Resume in 10 minutes for FREE
Build My Resume